Need to assess your cybersecurity posture?
Use the DERCF to evaluate the health of your distributed energy resource system.
ON THIS PAGE
- Why OT Cybersecurity Is Important
- Legislative Background
- Confidentiality Integrity Availability Triad
- Risks and Potential Consequences
- Types of Cybersecurity Attacks
- Understanding Your Cybersecurity Posture
- Additional Resources
- Glossary
According to the National Institute of Standards and Technology (NIST), operational technology (OT) refers to:
programmable systems or devices that interact with the physical environment (or manage devices that interact with the physical environment). Examples include industrial control systems, building management systems, fire control systems, and physical access control mechanisms.
It is important to distinguish the difference between OT and information technology (IT). NIST defines IT as "any equipment or interconnected system or subsystem of equipment that is used in the automatic acquisition, storage, manipulation, management, movement, control, display, switching, interchange, transmission, or reception of data or information by the executive agency."
Wind turbines, solar arrays, building control systems, and supervisory control and data acquisition (SCADA) systems are all examples of OT systems and are relevant to how our nation produces, stores, and manages energy. Many of these OT systems have IT components or connections. However, they each present significantly different vulnerabilities, risks, and consequences as it relates to securing them.
Why OT Cybersecurity Is Important
OT is becoming increasingly digital and internet-connected. This introduces security concerns for OT commonly used in federal facilities, where typically security had not been an issue before. Previously, most OT was non-connected and had minimal cybersecurity vulnerabilities—but as new efficiencies and functionalities for enhanced flexibility and resilience are added, cybersecurity vulnerabilities need to be continually monitored and addressed. As more connected technologies, control systems, and distributed energy resources are added to federal facilities, installations, and campuses, it is more important than ever to consider cybersecurity. Poor cybersecurity posture can result in vulnerabilities that leave a facility open to an attack that can result in data corruption, financial harm, physical equipment damage, disruption of services, and even loss of life.
Due to the complexity and cost of acquiring new equipment, technology, and operational systems, OT is frequently not replaced at the same rate as consumer or informational technologies. Thus, federal facility managers and operators face additional challenges in protecting legacy systems from cybersecurity threats, especially given that these systems are not likely to have the same cybersecurity protective capabilities as modern technology and may risk disruption if traditional IT cybersecurity protection and detection capabilities and solutions are applied.

Legislative Background
Several OT cybersecurity assessment and management legislative and policies and requirements have been put in place to improve safety and security.
Executive Orders
Executive Order (E.O.) 13636: Improving Critical Infrastructure Cybersecurity was released on February 12, 2013. To further prioritize cybersecurity for critical infrastructure, E.O. 13800: Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure was issued on May 11, 2017.
E.O. 13800 states that each agency head "shall use the Framework for Improving Critical Infrastructure Cybersecurity, which was developed by the National Institute of Standards and Technology, or any successor document, to manage the agency's cybersecurity risk." This framework is commonly known as the "cybersecurity framework."
NIPP
Additionally, the National Infrastructure Protection Plan (NIPP), developed by the U.S. Department of Homeland Security, names 16 crucial infrastructure sectors.
- Chemical
- Commercial facilities
- Communications
- Critical manufacturing
- Dams
- Defense industrial base
- Emergency services
- Energy
- Financial services
- Food and agriculture
- Government facilities
- Healthcare and public health
- IT
- Nuclear reactors, materials, and waste
- Transportation systems
- Water and wastewater systems
The NIPP provides unique language about the partnering of government and private sectors to manage risk and strengthen cybersecurity. Read more about NIPP and the resources it offers.
RMF and FISMA
Although the Federal Information Security Management Act (FISMA) is primarily geared toward IT, FISMA requires agencies to reference and follow the Risk Management Framework (RMF), a NIST document that includes OT devices and components in comprehensive cybersecurity assessments.
Federal energy managers are required manage OT cybersecurity to meet federal legislative, administrative, and agency requirements. Using various available frameworks, critical infrastructure owners and operators are guided to improve cybersecurity information sharing and collaboratively develop and implement risk-based approaches to cybersecurity. The table below lists FEMP tools to that can help federal energy managers manage OT cybersecurity challenges.
| FEMP OT Cybersecurity Tools for Federal Energy Managers | ||||
|---|---|---|---|---|
| Framework | Origin | Required by | User | Available FEMP Tools |
| NIST Cybersecurity Framework | NIST 800-53 | E.O. 13636, E.O. 13800 | IT, OT, facilities in government and industry | Facility Cybersecurity Framework, Distributed Energy Resource Cybersecurity Framework (DERCF) |
| Cybersecurity Capability Maturity Model | U.S. Department of Energy | Administration Request | IT, OT, cyber experts | Facility Cybersecurity Capability Maturity Model, DERCF |
| Risk Management Framework | NIST 800-37 | FISMA | Team of cyber, facilities, IT | FCF-Risk Management Framework Hybrid Tool |
| Cybersecurity Maturity Model Certification | U.S. Department of Defense (DOD) | DOD | Team of cyber, facilities, IT, procurement | N/A |
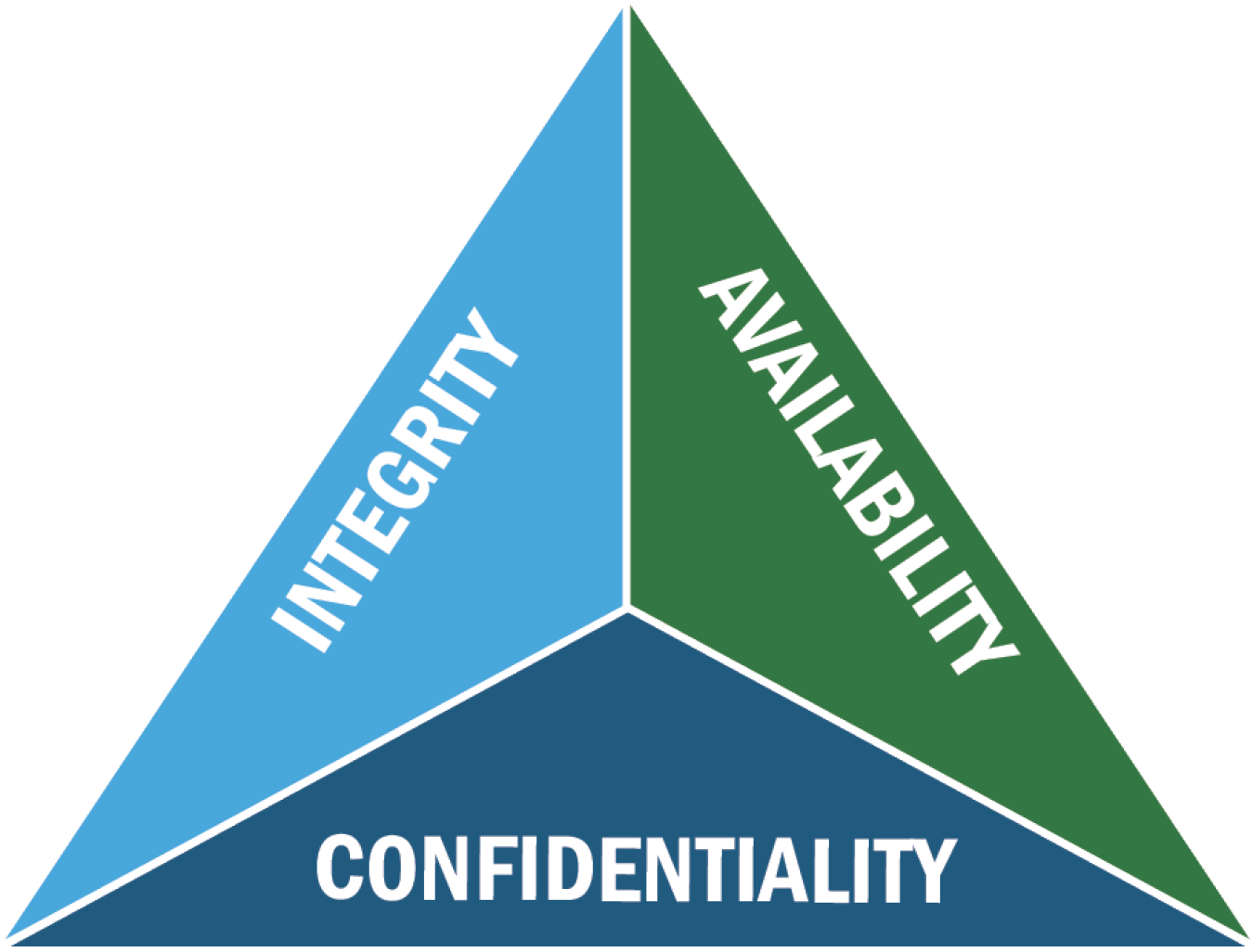
Confidentiality Integrity Availability Triad
The frameworks in the table above contain a collection of controls that are designed to lower the risk of cybersecurity attacks by providing context for technical implementation and cybersecurity governance. To understand the basis for cybersecurity risks within the scope of OT, it is important to first understand the Confidentiality Integrity Availability (CIA) triad reference developed by FISMA.
The CIA triad is a model used to represent three core principles: confidentiality, integrity, and availability. The challenge to create and maintain all three principles simultaneously in informational and operational technology spaces is known as cybersecurity.
CIA Triad Principles
NIST defines confidentiality as "preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information."
The confidentiality principle of the CIA triad is what protects the privacy of potentially sensitive data. While this commonly includes encryption (which is a powerful technique) other tactics include strong methods for access control, authorization, and authentication.
NIST defines integrity as "Guarding against improper information modification or destruction and includes ensuring information non-repudiation and authenticity."
Maintaining integrity means ensuring that information is valid and hasn't been altered by anyone on its way to the destination. For example, this can be done by generating a unique identifier for a file and verifying that the identifier is the same when re-generating upon receiving a file.
NIST defines availability as "Ensuring timely and reliable access to and use of information." The availability principle of the CIA triad strictly focuses on ensuring systems are functioning properly when they need to. In the case of energy systems, this means keeping the lights on. In other industries, this might be more associated with data availability, or another service such as entertainment.
While the principles of the CIA triad are geared toward the IT space, it is important to note that security for OT systems is typically weighted differently than for IT. For example, availability is absolutely critical to the cyber-physical world whereas confidentiality and integrity, which are critical in IT, may be differently prioritized for OT systems.
Disrupting the availability of an energy system immediately and directly affects consumers and their access to electricity. These principles are further integrated into the Standards for Security Categorization of Federal Information and Information Systems (FIPS 199) by defining three levels of potential impact for each CIA triad principle.
Risks and Potential Consequences
It is important to understand what cybersecurity risks exist, how these risks are unique in the context of OT, and the potential challenges they bring in terms of mitigation. According to NIST, risk is defined by "the level of impact on organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals," which result from the standard operation of a system due to the potential adverse effects of a cybersecurity threat.
Since there is no such thing as a perfectly secure system, there will always be some type of risk that needs to be addressed. Utilizing the NIST Risk Management Framework is an essential step to understanding and prioritizing cybersecurity risks.
Supply chain risk is defined by NIST as "the risk that an adversary may sabotage, maliciously introduce unwanted function, or otherwise subvert the design, integrity, manufacturing, production, distribution, installation, operation, or maintenance of an item of supply or a system so as to surveil, deny, disrupt, or otherwise degrade the function, use, or operation of a system."
Oftentimes this is a risk that slips under the radar but can cause significant issues. Downstream supply chain risk can put a site at risk for serious privacy concerns, risk of disruption to availability, as well as the potential for hardware/software vulnerabilities that are not publicly documented.
According to NIST, a vulnerability is a "weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source."
Common sources of vulnerabilities across OT within energy systems include but are not limited to:
- Sensors, controls, and communications: Cyber-physical convergence of IT/OT can constitute a new attack surface.
- Power electronics: Enhanced performance capabilities but with hardware that may have vulnerabilities.
- Connectivity: Energy efficiency and renewable energy technologies are increasingly internet- and grid-connected, allowing for new opportunities at the cost of increased attack surface.
- Legacy systems: Lack basic cyber defenses. The age of a legacy system can make it impossible to update or change.
- Internet and grid connections: Due to the cyber physical nature of energy systems, there is an enhanced motive for attackers to have a direct impact on components in the real world.
Physical harm and monetary losses are common consequences due to "availability" being an attractive target to attackers. Cyberattacks can cause physical damage to equipment. For example, running machines at different speeds can result in mechanical damage including immediate damage, increased wear and tear over time, or even harm to people nearby.
Due to cost and complexity, equipment in the energy sectors is replaced less often than consumer products such as computers and phones. Physical damage requiring serious repairs or even replacement is a major impact to organizations or federal facilities—and tends to be very expensive.
Types of Cybersecurity Attacks
Cybersecurity attacks come in a variety of flavors, though each type targets one or more of the three CIA triad principles. Types of cybersecurity attacks include the following.
Eavesdropping (Confidentiality)
According to NIST, eavesdropping is an "attack in which an attacker listens passively to the authentication protocol to capture information that can be used in a subsequent active attack to masquerade as the claimant." Eavesdropping can pose a threat to control systems in that an attacker can gain access to commands, set points, and other sensitive information relevant to cyber physical systems, which may aid them in carrying out a more elaborate attack.
Misconfiguration of Settings/Data Injection to Cause Abnormal/Harmful Behavior (Integrity)
While it is not a complex tactic, the modification of data, settings, or default setpoints can have a disastrous outcome in OT environments. The physical nature of OT cyber systems leaves them susceptible to integrity attacks such as false data injection or the malicious modification of settings that may remove preconfigured safety settings. This, in turn, could cause machinery to operate at conditions outside of a safe threshold thus endangering equipment and personnel.
Denial of Service (Availability)
NIST defines denial of service as "the prevention of authorized access to resources or the delaying of time-critical operations." Often, this is the result of sending copious amounts of traffic to a server and rendering it incapable of responding to legitimate requests by operational equipment. Traffic originating from many different sources is known as a distributed denial of service, or DDoS, attack, making it very difficult to trace. This can very quickly compromise the availability of energy and electricity to a population.
Note that many tactics and techniques can be used in conjunction with each other. For a helpful reference on tactics and techniques used in cyberattacks on industrial control systems, visit MITRE ATT&CK for Industrial Control Systems.
Real-World Cybersecurity Attack Examples
The following are examples of real-world and research scenarios indicating potential weaknesses in energy systems and facilities.
Wind Turbine Hack
A 2017 Wired.com article titled "Researchers Found They Could Hack Entire Wind Farms" demonstrated how easy it can be to take control over a wind farm if the proper physical and cyber precautions aren't taken. Utilizing a Raspberry Pi, an attacker was able to intercept messages headed to the turbine controller and stop the turbine from turning. This is just one example. Penetration tests can provide a shocking look at how vulnerable a component or collection of components can be and highlight potential outcomes should a real attacker gain access. Allowing the control of OT to fall into the wrong hands can result in extreme consequences including damage or destruction to components.
Building Automation System Hack
An attack on a building automation system (BAS) in Finland rendered heating systems completely inoperable due to a denial of service attack. For several days, computer systems attempted to reboot themselves which only prolonged the outages. A combination of lack of awareness/training and poor Internet of Things configuration created an opportunity for attackers to take advantage of the situation.
While not comprehensive, the above examples provide context for the variety of attacks on OT systems and their potential effects if risks are not appropriately addressed.
Understanding Your Cybersecurity Posture
The Federal Energy Management Program (FEMP) assists organizations with determining their cybersecurity posture and current vulnerabilities and identifying acceptable and unacceptable levels of risk. Being aware and informed is the first step to addressing cybersecurity issues. While cybersecurity risks cannot be entirely eliminated, there are a number of measures that can be taken once threats and vulnerabilities are identified.
Access Control
Access control authenticates and authorizes individuals to access information. For example, if a facility has a BAS, good cyber hygiene could limit access to building data to only those users who need that information to conduct their job duties—and they would only see the specific information necessary for their role ("least privilege"). When users no longer need to access specific building data, their access would be removed. Administrators would also ensure that passwords to access the BAS data are quickly changed from defaults, are regularly changed, and are unique to each user of the system.
Patch Management
Patch management helps identify, install, and verify patches for products and systems that address potential security vulnerabilities or other issues. While it may be difficult to implement an automatic update routine for older OT systems, it is extremely important to update software and firmware when possible, as running old code can leave a system very easily exploitable.
Asset Management
For small and large organizations, maintaining an effective and consistent asset management policy facilitates visibility into the environment and helps ensure that devices can be accounted for. Sites should have a regularly updated inventory of devices that includes OT systems such as meters, gateways, remote terminal units, and other components.
This inventory will serve as a helpful reference during normal operation as well as during a potential cybersecurity incident. Additionally, maintaining an up-to-date network configuration diagram provides detailed context for maintenance, system changes, or response/recovery in the event of an attack. This includes any connections from OT systems to the IT or enterprise network.
Network Hardening
Hardening is the process of eliminating a means of attack by addressing vulnerabilities and turning off non-essential services. The separation between the IT and OT network is critical to reducing the potential attack surface to OT. Phishing is one of the most common attacker entry points into an IT environment but is still a serious threat to OT. Lack of separation of networks may provide an opportunity if an attacker obtains credentials though a successful phishing campaign. It is important to remove outside "rogue" connections/circuits and close unused ports—for example, disabling functionality of a webserver on a device that does not require it. This simple step can remove an opportunity for attackers to have unauthorized access to a device that was simply poorly configured.
Cyberattack Response/Recovery Plan
In the event of a cybersecurity incident, a quick and effective response plan is essential to preventing a bad situation from becoming catastrophic. Planning and proper documentation are two critical aspects of developing an appropriate cybersecurity response and recovery plan. This includes identifying and assigning responsibilities, sharing information, and reviewing and updating as changes to the environment occur. The NIST Guide for Cybersecurity Event Recovery provides detailed information for understanding the cybersecurity recovery process.
Contract Language
Due to the reliance on third-party vendors for hardware and software for energy delivery systems, it is important to consider cybersecurity from a contractual language perspective. This includes but is not limited to supplier software requirements, suggestions for documentation, and addressing cybersecurity lifecycle issues. For more information on cybersecurity procurement, see Pacific Northwest National Laboratory's Guide on Cybersecurity Procurement Language. It serves as a starting point reference to federal facility cyber procurement as it relates to OT specifically.
See FEMP's Energy and Cybersecurity Integration page for resources to help you understand your cybersecurity posture.
Additional Resources
- Training Available Through the U.S. Department of Homeland Security Cybersecurity and Infrastructure Security Agency
- Purdue Enterprise Reference Model (ISA-99)
Glossary
The table below provides terminology and definitions for concepts related to OT and cybersecurity. Definitions denoted with an asterisk are credited to NIST.
| Term | Definition |
|---|---|
| Critical infrastructure* | Systems and assets, whether physical or virtual, so vital to the U.S. that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters. |
| Distributed energy resources | Small, modular energy generation and storage technologies that provide electric capacity or energy where you need it. |
| Industrial control system* | An information system used to control industrial processes such as manufacturing, product handling, production, and distribution. Industrial control systems include supervisory control and data acquisition systems used to control geographically dispersed assets as well as distributed control systems and smaller control systems using programmable logic controllers to control localized processes. |
| Information technology/operational technology (IT/OT)* | IT speaks the language of computers and networks that support utility business administrative processes. OT speaks the language of electronic devices with embedded operating systems streamlined to support energy delivery functions and operational networks. |
| Legacy system | A custom environment containing older systems or applications that may need to be secured to meet today's threats, but often use older, less secure communication mechanisms and need to be able to communicate with other systems. |
| Phishing* | A technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation via email or a web site, in which the perpetrator masquerades as a legitimate business or reputable person. |
| Power electronics | Power electronics convert alternating current to direct current, or to alternating current at different voltage or frequency. |
| Sensor | A device that detects or measures, then analyzes and responds to physical property and records. |
| Supervisory control and data acquisition (SCADA) | A computer system that monitors and controls a process. |
| Threat (cybersecurity)* | Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service. Also, the potential for a threat source to successfully exploit a particular [operational] system vulnerability. |

FEMP's Cybersecurity Considerations for Performance Contracts

